Meet TrapNET
Draw attackers out into the open with intrusion-based detection and contextual intelligence.
TrapNet is a tool developed to help companies that provides cybersecurity services to detect breaches early with minimal effort. It’s easy to set up, requires no ongoing maintenance, and has no false positives. By reducing alert fatigue and improving threat detection and response, TrapNet generates great value for those organizations struggling with complex security operations and resource limitations.
What is TrapNet
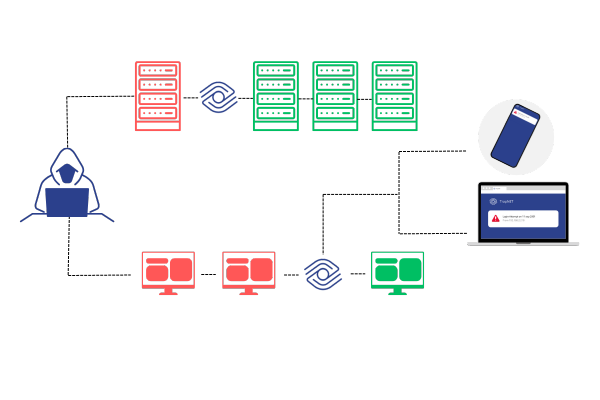
It is a Deception/Canary technology that allows the creation of several Realistic Decoys like fake systems, services or traffic, to attract, detect and TRAP attackers during the early reconnaissance stages. TrapNet provides High-Fidelity Alerts because it is only triggered when the attackers interact with the fake assets, ensuring that alerts are accurate and actionable.
Why TrapNet
Evolving Threat Landscape
Cyber-adversaries that use advanced tools and tactics like generative AI for phishing, outpaces traditional security measures.
Expanding Attack Surface
The growth of remote work, third-party connections,
and digital transformation increases vulnerability.
Alert Overload
The high volume of security alerts and false positives overwhelms
security teams.
Operational Complexity
Managing and maintaining numerous security tools adds to the operational burden, often leading to misconfigured controls and increased risks.
Threat Detection & Response
It takes an average of 168 hours or more. Many
threats go undetected.
Conclusion
Threats & Breaches are very difficult to prevent, very hard to detect,
and remediate them consumes a lot of resources.
enhances threat detection and response through ease of use, automation, and actionable
intelligence, And the best of all, at a price anyone can pay!
How It Works
1
Preconfig
Download and install TrapNet software into one or several dedicated
devices.
2
Deployment
Set up TrapNet with fake but realistic services and deploy them
across your network. Do not worry, TrapNet’s engineering team can help you.
3
Monitoring
TrapNet runs silently, waiting to detect unauthorized access.
4
Alerts
When an attacker interacts with TrapNet, it sends an immediate alert.
TrapNet integrates with existing security tools to improve detection and generate real-time blocking rules.
Key Features
Quickly deploys fake assets and tokens without complex configuration.
✓ Effective Alerts
Sends notifications only when significant activity and interaction with decoys is detected.
✓ Low Maintenance
Once deployed, TrapNet works quietly in the background.
✓ Integration
Works and integrates with other security tools.
✓ Dynamic Updates
Automatically refreshes fake assets based on changing threats and network conditions.
✓ Automatic Attack Isolation
Isolates threats automatically, blocking spread and command server communication, with SIEM/SOAR integration.
Puts compromised endpoints into quarantine to prevent attack spread within the network.
✓ Internal Threat Detection
Identifies and diverts attacks, detecting reconnaissance and lateral movement with fewer false positives.
Captures and analyzes real-time attack activities, providing detailed forensic analysis and collecting IOC and TTP.
Additional Tools
TrapNet Tokens: Small, fake tokens that alert you if they are used, indicating a breach.
Advantages Over Traditional Honeypots
✓ Security:
TrapNet discloses any vulnerabilities and is designed to be resilient even if attacked.
✓ Ease of Use:
TrapNet is easy to deploy and manage compared to traditional honeypots.
✓ Simple Alerts:
Focused on clear, actionable alerts rather than complex anomaly detection.
Overall, TrapNet offers a straightforward and effective solution for early breach detection with minimal hassle.
Seamless Security for SCADA, IoT, and Integrated OT Systems
Extend your security to OT Environments: TrapNet emulates OT and IoT devices to protect against threats in these complex environments. TrapNet Supports various environments with specific decoys for SCADA systems, IoT sensors, and more, making it ideal for organizations with limited security resources or those integrating IT and OT environments.
